4.7. Managing Users and GroupsIn an age of viruses, worms, and identity theft, keeping information private and secure has taken on great importance. Managing user identity creates the framework for system securityeven on a single-user system, where a distinction is maintained between using the system as the normal user and using the system as the root user. 4.7.1. How Do I Do That?Almost everyone identifies themselves as both an individual and as a member of several groups. Linux uses separate user and group identities to reconstruct this two-level structure inside the system. For example, company employee Richard might be all of the following:
(And that doesn't even touch on life outside of the company!) The system administrator configures Richard's account to indicate his many involvements within the company. At the user level, the name richard is assigned to him, and a password and home directory are assigned. richard is then placed into the groups it, toronto, acmeproposal, christmas, and soccer. Fedora Core extends this system using a scheme called user private group (UPG), which means that Richard also has his own private group, also named richard. UPG makes a lot of sense when you look at permissions. 4.7.1.1. Managing users graphicallyThe Fedora GUI tool for managing users and groups is
system-config-users, which is accessed through the menu under System Figure 4-8. The Users and Groups configuration window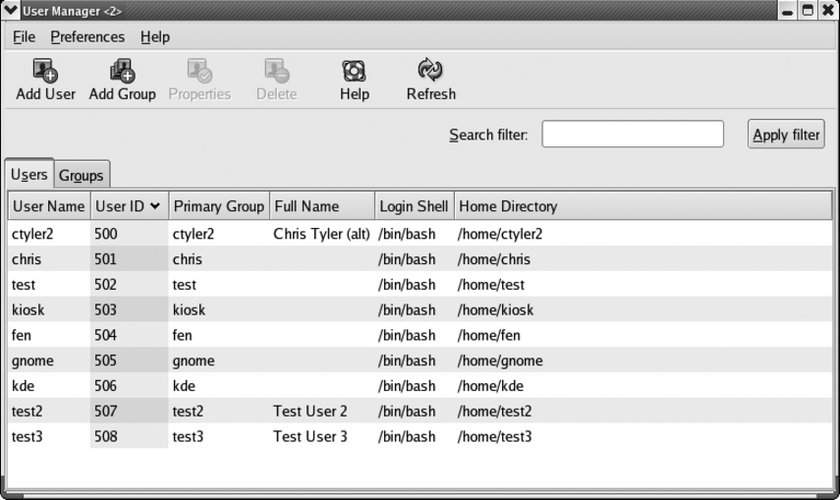
This window has two tabs, one for managing groups and one for managing users. To add a user, click on the Add User icon. The window shown in Figure 4-9 will be displayed. Figure 4-9. The Create New User window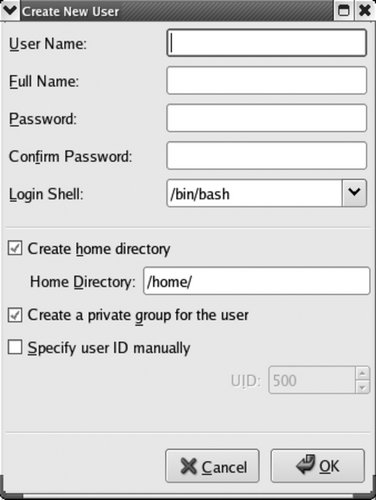
Fill in each of the fields:
Once you have filled in all of these fields, click OK. You will be returned to the main User and Group configuration window (Figure 4-8). To edit a user, double-click on the user's name, or highlight the name and click the Properties icon. An edit window will appear with four tabs, enabling you to edit values that cannot be set during the creation of the account; Figure 4-10 shows each of these tabs. Figure 4-10. The four tabs of the User Properties window
The four tabs are:
The value of password aging is debatable; while it does limit the time that a compromised password can be used, forcing a user to change her password too frequently can make it difficult for her to remember the current password, leading to unsafe practices such as writing passwords on sticky notes or choosing weak passwords. To delete a user account, click on the username and then click on the Delete icon. You will be warned if the user account is active (i.e., if the user is logged in or has processes running), and you will be asked for confirmation. The confirmation dialog has a checkbox that controls whether the user's files will be deleted along with the user account. If you are planning to keep the user's files, it may be better to lock the account than to delete it, so that the user's name continues to show up as the owner of those files (if the account is deleted, the account number is shown instead of the name). 4.7.1.2. Managing groups graphicallyThe Group tab of the User Manager window works in exactly the same way as the Users tab. The only fields that appear in the Add Group dialog are for the group name and, if you want to set it manually, the group number. The Properties dialog adds a tab that shows you a list of all of the users on the system, with checkboxes to indicate which ones are in the group. 4.7.1.3. Adding and managing users from the command lineFedora provides six utilities for managing users and groups from the command line. For users, there are useradd, usermod, and userdel; for groups, there are groupadd, groupmod, and groupdel. The express way to add a user is to use useradd and then set the new user's password using passwd: # useradd jane
# passwd jane
Changing password for user jane.
New UNIX password:
bigSecret
Retype new UNIX password:
bigSecret
passwd: all authentication tokens updated successfully.useradd accepts a number of options; the most common are shown in Table 4-12. Most of these options can also be used with usermod to change an existing user's options.
To set Jane's full name when her account is created, execute: # useradd -c "Jane Smith" jane usermod works in a similar way to useradd, but is used to adjust the parameters of existing accounts. For example, to change Jane's full name: # usermod -c "Jane Lee" jane As you'd expect, the userdel command deletes a user. The -r option specifies that the user's home directory and mail spool (/var/spool/mail/ user) should also be removed: # userdel -r jane The groupadd, groupmod, and groupdel commands are used in a similar way to create, modify, and delete groups. To add a group, just specify the name as an argument to groupadd: # groupadd groupname The only option commonly used is -g, which lets you manually select the group ID (useful if converting data from an old system): # groupadd -g 781 groupname The groupmod command is rarely used, but it will change the numeric group ID (-g) or the name (-n) of an existing group: # groupmod -g 947 groupname # groupmod -n newname groupname To delete a group, use groupdel: # groupdel groupname 4.7.1.4. Managing user passwords from the command linepasswd is used to set a user's password. Used by a normal user, it sets that user's password by asking for the current password and then asking for the new password twice: $ passwd
Changing password for user chris.
Changing password for chris
(current) UNIX password:
bigSecret
New UNIX password:
newSecret
Retype new UNIX password:
newSecret
passwd: all authentication tokens updated successfully.When used by the root user, passwd can be used to change the root password (the default) or any existing user's password if the username is supplied as an argument. You don't need to know the current password: # passwd
Changing password for user root.
New UNIX password:
topSecret
Retype new UNIX password:
topSecret
passwd: all authentication tokens updated successfully.
# passwd jane
Changing password for user jane.
New UNIX password:
superSecret
Retype new UNIX password:
superSecret
passwd: all authentication tokens updated successfully.The root user can also delete a password from an account (so a user can log in with just a username): # passwd -d jane Removing password for user jane. passwd: Success This must be used carefully because it presents a big security risk. Remember that remote users may be able to connect via SSH, and then they won't need a password either! To find out the password status of an account, use -S: # passwd -S jane Empty password. # passwd -S chris Password set, MD5 crypt. 4.7.1.5. Managing groups and delegating group maintenance from the command lineThe gpasswd command can be used to set a group password. This is rarely done. However, it is also used to manage groups and, better yet, to delegate group administration to any user. To specify the members of a group, use the -M option: # gpasswd -M jane,richard,frank audit In this case, jane, richard, and frank are made members of the audit group. Any previous memberships in that group will be obliterated, so only these three users will now be in that group. (Other group memberships held by those users will not be affected.) You can also add or delete individual group users using the -a and -d options: # gpasswd -a audrey audit # gpasswd -d frank audit Those commands add audrey to the group audit, then delete frank. If you delegate group administration to users, they can use the -a and -d optionsa great labor-saving idea! Delegation is performed with the -A (administrator) option: # gpasswd -A jane audit jane$ gpasswd -a matthew audit 4.7.2. How Does It Work?User accounts are controlled by the /etc/passwd file, which looks like this: root:x:0:0:root:/root:/bin/bash bin:x:1:1:bin:/bin:/sbin/nologin daemon:x:2:2:daemon:/sbin:/sbin/nologin adm:x:3:4:adm:/var/adm:/sbin/nologin ...(Lines snipped)... fax:x:78:78:mgetty fax spool user:/var/spool/fax:/sbin/nologin nut:x:57:57:Network UPS Tools:/var/lib/ups:/bin/false privoxy:x:73:73::/etc/privoxy:/sbin/nologin chris:x:500:500:Chris Tyler:/home/chris:/bin/bash diane:x:501:501:Diane Tyler:/home/diane:/bin/bash jane:x:502:502:Jane Smith:/home/jane:/bin/bash richard:x:503:503:Richard Lee:/home/richard:/bin/bash The fields in this file are separated by colons. From left to right, they are:
Since /etc/passwd must be readable by everyone so that commands such as ls -l can function correctly, the passwords have been moved to a file that is readable only by root, named /etc/shadow, which looks like this: root:$1$45ZWBaPE$XvzhGEj/rA4VDJXdQESi0.:13024:0:99999:7::: bin:*:13024:0:99999:7::: daemon:*:13024:0:99999:7::: adm:*:13024:0:99999:7::: ...(Lines snipped)... fax:!!:13024:0:99999:7::: nut:!!:13024:0:99999:7::: privoxy:!!:13024:0:99999:7::: chris:$1$hUjsHJUHIhUhu889H98hH.8.BGhhY79:13068:0:99999:7::: diane:$1$97KJHNujHUkh88JHmnjNyu54NUI9JY7:13024:0:99999:7::: jane:$1$yuaJsudk9jUJHUhJHtgjhytnbYhGJHy:13024:0:99999:7::: richard:$1$pIjyfRbKo71jntgRFu3duhU97hHygbf:13024:0:99999:7::: Note that the second field contains an encrypted version of the password. The encryption function, called a hash, is not reversible, so it's not possible to take this data and reconstruct the password. When the user enters his password, it is also encrypted; then the two encrypted values are compared. The other fields in this file contain information used for password aging (expiry). In a similar way, /etc/group contains basic information about each group: root:x:0:root bin:x:1:root,bin,daemon daemon:x:2:root,bin,daemon sys:x:3:root,bin,adm adm:x:4:root,adm,daemon ...(Lines snipped)... fax:x:78: nut:x:57: privoxy:x:73: chris:x:500:fen diane:x:501: jane:x:502: richard:x:503: audit:x:504:jane,richard soccer:x:505:richard,jake,wilson,audrey,shem,mike,olgovie,newton toronto:x:506:matthew,jake,wilson,richard,audrey,shem,mike,olgovie,newton,ed,jack ...(Lines snipped)... The fields here are:
The /etc/gshadow file contains the actual passwords, plus group administrator information: root:::root bin:::root,bin,daemon daemon:::root,bin,daemon sys:::root,bin,adm adm:::root,adm,daemon ...(Lines snipped)... fax:x:: nut:x:: privoxy:x:: chris:!:500::fen diane:!:501:: jane:!:502:: richard:!:503:: audit:!:504:jane:jane,richard,audrey,matthew soccer:!:505:richard,jake:richard,jake,wilson,audrey,shem,mike,olgovie,newton toronto:!:506:ed:matthew,jake,wilson,richard,audrey,shem,mike,olgovie,newton,ed ...(Lines snipped)... The group administrators are in field 4 and group members are in field 5 in this fileso in this case, jane is the group administrator for audit, and jane, richard, andrew, and matthew are group members. 4.7.3. What About...4.7.3.1. ...the kuser program on the menu?kuser is a KDE program that provides an alternative to system-config-user. The two programs are functional duplicates, but I think system-config-user looks better. 4.7.3.2. ...editing the password and group files directly?It is possible but must be done carefully to avoid leaving the system in an unusable state. The vipw and vigr scripts provide the most convenient way of editing these files; vipw edits /etc/passwd and /etc/shadow, and vigr edits /etc/group and /etc/gshadow. In both cases, the files will be locked to prevent concurrent changes by another program, and the vi editor will be used for editing (the EDITOR environment variable can be used to specify another editor if you'd prefer). 4.7.3.3. ...checking that the password and group files are properly written?The pwck command can be used to check and repair /etc/passwd and /etc/shadow: # pwck user adm: directory /var/adm does not exist user gopher: directory /var/gopher does not exist user ident: directory /home/ident does not exist user torrent: directory /var/spool/bittorrent does not exist invalid password file entry delete line \Q'? y pwck: the files have been updated grpck performs similar checks on /etc/group and /etc/gshadow: # grpck invalid group file entry delete line \Q'? y invalid group file entry delete line \Qascasdcasdarg asdfasdf'? y grpck: the files have been updated 4.7.4. Where Can I Learn More?
|