As you have seen, NLB is a great way to enhance scalability and availability in a large Web server cluster. But as you certainly understand, a large cluster of computers will present some difficulties. These you must overcome if you want your applications to work properly. You must address three key issues when building a large Web solution. We have discussed them before, but they are important, so we will go over them again and see what problems they might present.
Availability: You cannot accept a Web site that is not accessible to your visitors. Often you need the site to be up and running 99.999 percent of the time. This does not leave much room for the type of maintenance that might require you to take the servers down. Do the math and see. Network Load Balancing helps you reach this goal by letting many servers appear externally as one. But with a large cluster, how can you manage the servers and still keep your sanity?
Scalability: As your Web site grows more and more popular, the load increases. Even with a cluster of Web servers, you will eventually reach a limit for how much it can take. This is why you need a way to add more power easily without interrupting the site. You just do not have the time to take the cluster down, reconfigure it to use more servers, and then take it online again.
Manageability: This topic might seem obvious now after presenting some of the problems with a large cluster. But there is more to this than managing the servers. You must also find ways to update your Web site content in an easy manner when you have a large cluster. When you have many servers, you must update every server very quickly to make the same content available on all servers. Doing this manually would take a long time for administrators. These people have much more important things to do, trust us.
Microsoft technicians have seen these problems too. They manage one of the world's largest Web sites themselves and realized this a long time ago. That is why they have developed a great tool to make life easier. Application Center is a management and deployment tool designed to solve these three issues. But as you will see, Application Center can do wonders for the business tier, too.
A cluster is a set of servers that serve the same content to cluster users. It can handle HTTP requests as well as DCOM requests. Application Center is designed to handle two of the tiers in a multitiered solution. We have already talked about the user interface in terms of a Web site cluster. The clients accessing this tier can be either thick (that is, a Windows application), or thin (which means a Web browser client). Especially with the Web services technique, which will be discussed in another chapter of this book, it is easy to incorporate a Web service into a thick client. The clusters discussed so far in this chapter have been Web clusters handling HTTP requests.
But Application Center also handles DCOM clusters, which makes it good for managing the business tier as well. Business logic often is a set of COM+ components or assemblies in .NET. These components serve the purpose of separating the logic from user interface and database access, thus making it more general and accessible to all sorts of applications. The traffic on this tier can be great, especially if it is serving a large Web cluster as well as many other applications on the network. Therefore you must find a way to scale this tier. You can do this by using Component Load Balancing (CLB), which is included with Application Center. Figure 3-7 shows a schematic overview of a Web site solution using Application Center to handle load balancing.
Application Center clusters are designed for stateless, middle-tier applications, such as Web sites and COM+ applications. We will talk more about state and state handling later in this chapter, so we will leave this discussion for now. As opposed to Windows clustering, Application Center clusters do not need to share a common disk array and do not need to use special hardware.
Let's take a look at the Application Center feature set. It has four major features as we see it:
Cluster services and load balancing
Synchronization and deployment
Monitoring
Administration
These features all help to solve the problems described earlier. Cluster services and load balancing help in maintaining scalability and availability. Synchronization helps when you need to add new content or update content in your solution. It also helps when deploying a new application. Administration and monitoring help you by providing greater manageability, thus making it easier to control all the servers from one single point.
Application Center includes several wizards (such as the one in Figure 3-8) and a user interface based on Microsoft Management Console (MMC). These tools help the administrator by making it easier to create and manage clusters.
Application Center supports the following types of clusters (see Figure 3-9):
General cluster (Web-tier)
COM+ application cluster
COM+ routing cluster
A general cluster is nothing but a group of servers processing client requests. In this category you find the Web server cluster, which is the kind of cluster this chapter focuses on, in addition to database clusters, staging clusters (aka deployment servers) and stand-alone clusters. Yes, you read correctly. A stand-alone cluster is a cluster with only one member, which you will learn more about later in this chapter. A few other clusters also fit in the general category, but these are the most important ones.
The most common cluster using Application Center would be a Web server cluster that hosts Web sites as well as local COM+ components (or assemblies in .NET). These clusters can use several load-balancing techniques. Application Center does not care if you use load-balancing techniques other than Network Load Balancing. In Figure 3-10, you can see that during setup of a new cluster you can choose the type of load balancing you will use. You still get the advantages of clustering several servers that we have already discussed.
A typical scenario using Network Load Balancing might look like Figure 3-11. Application Center in this scenario eases the task of administering the cluster. Adding and removing (setting members online or offline) is handled through the Application Center user interface.
Because Network Load Balancing dynamically distributes client workload even when you set members online or offline, the site is available during the whole process. This makes it easy to add more power to your site by adding servers during runtime.
We mentioned single-node clusters. You might think they seem strange, since a cluster by definition ought to use more than one server. But sometimes it can be useful to operate Application Center on a single server, without the multi-member cluster context. If you use Application Center on a single-node cluster, it treats this cluster as a one-member cluster, which it in fact is. This is typically useful when you need a stager or a staging area—that is, a server where you publish content before you actually deploy it on the production cluster. This provides a way of testing quality and functionality from development and testing environments before going live with your site. Because the stager does not need to be as powerful as the production cluster, you can use a simpler cluster but still keep the Application Center functionality.
In the Web pages of a Web application, different components are instantiated to serve the application with data of various sorts. You could, for instance, have an application where a salesperson looks up customer data by calling a COM+ component that has a function named GetCustomerData. It really does not matter whether the application is a Web application or if it is a thick Windows client, the instantiation is the same. If the GetCustomerData component resides on a different server than the application itself, and there are many users accessing this component, the workload on the server can be immense. To ease the pressure on the server, you can create a cluster of servers to handle these COM+ components, just as you might do with your Web site. The benefits of doing this are the same as for Network Load Balancing described earlier. Application Center COM+ clusters load balance the method calls to instantiate the components across multiple cluster members within the COM+ cluster. A simplified scenario of this is shown in Figure 3-12. This cluster uses Network Load Balancing as a load balancer.
To support Windows-based clients using DCOM, the cluster can understand DCOM calls and use Network Load Balancing to distribute these incoming client requests.
But in a more likely scenario than the one just described, the layering of the application would be different. To ease the load on the Web cluster, the COM+ components would probably be moved to their own cluster and Component Load Balancing would be used to load balance the activation requests for the COM+ components as shown in Figure 3-13.
In the scenario in Figure 3-13, we have also included something called a COM+ Routing Cluster. This cluster is located on the Web servers and uses Component Load Balancing to route requests for COM+ components from the general cluster to the COM+ Application Cluster. COM+ Routing Clusters are not really necessary, but serve their purpose when you need to load balance COM+ requests from a general cluster across multiple COM+ Application Clusters. This depends on a limitation in the Application Center 2000 release of Component Load Balancing that makes it possible for CLB to have only a single list of remote servers for every routing server. Otherwise, Web clusters can communicate with COM+ clusters over load-balanced DCOM without a COM+ Routing Cluster, since each Web cluster member acts as its own router for choosing the right COM+ server to handle component activation.
If you develop a new application entirely in .NET, you would not use COM Interop, of course. In this situation, you would use .NET Remoting with binary formatting either over HTTPChannel or over TCPChannel. You can scale .NET Remoting hosted in IIS just as you scale your Web clusters, and performance is high as well. The one thing you need to remember is that this only works when you use .NET Remoting hosted in IIS. When it comes to .NET Remoting outside IIS, we have not yet found a way to scale this, but suspect future versions of Application Center will solve this limitation.
On the other hand, when you have an integration project and cannot change the old components, CLB is a good way to enhance performance.
The fastest way of activating components is by having them on the local machine of the user (or Web server, if it is a Web application). But by using the scenario in Figure 3-13, you get a lot of other benefits that clearly outnumber the use of local components:
COM+ Application Clusters can accept requests from both thin and thick clients. That is, they can handle both Web browser–based clients as well as Windows-based clients. This means you can reuse business logic in many applications.
If the COM+ components reside on the Web server, they could consume resources, making the server unresponsive. You cannot let this happen. Otherwise, you may as well abandon the idea of the five nines (99.999 percent uptime). By creating a separate cluster for the components the Web server is relieved and can continue to handle client requests with better performance.
To gain higher security, you can also place the component cluster behind a separate firewall. By doing this, you will restrict clients accessing the Web cluster from also being able to access the components. You will see more about this later in the chapter.
Since you isolate COM+ applications on a separate cluster, you accomplish higher manageability. By having two clusters, you make it possible to have different developers and administrators maintain each cluster independently. Of course, this requires a large organization with lots of resources. This is nothing for the small Web site, obviously, which would not need load balancing anyway.
You use a wizard to set up and configure Network Load Balancing in Application Center. This wizard, the New Cluster Wizard, quickly sets up and configures Network Load Balancing (refer back to Figure 3-8). Remember, this is the same wizard you use for setting up any load balancer, as Figure 3-10 showed. You do not need to configure anything during this process; the wizard handles everything. However, if you do not like the default values, you can easily change them by using the Application Center user interface after you have created the new cluster (see Figure 3-14).
The user interface makes it easy to add and remove cluster members once you are up and running with the cluster. This is also the place to go if you need to change other aspects of your Application Center configuration.
One thing to do before running the Application Center setup is making sure that you have at least two network interface cards. You will need to have one card for handling internal communication within the cluster and one for handling communication with clients. The latter card needs to have at least one static IP address that is used as the cluster IP address, or as we refer to it, the virtual IP address. This is the address clients use to access the cluster.
We stated earlier that Application Center helps in synchronizing the cluster and in deployment of an application. First, let us explain what we mean by an application. An application in this context can contain a complete Web site with all of its content, like Web pages, COM+ components, system settings, and any other content that must exist on each cluster member for the solution to work properly. But it can also be a COM+ application intended only for the business tier. (By the way, guess where the name Application Center came from.)
To synchronize the cluster when, for example, developers make updates to a Web page, Application Center uses an image of the application. The image can, of course, contain one or more applications if needed. When a new application with all its content is ready for deployment from the staging cluster, an initial application image is created. This image is then copied by Application Center to a cluster controller on the production cluster and then replicated to all member servers. The controller maintains the latest, most accurate content for the cluster. When an update occurs in any of the application content on the controller, changes are synchronized automatically to each of the other cluster members. If you want to, you can manually perform this synchronization.
As you can see, Application Center certainly eases the job for administrators. But keep in mind that what we have been talking about here is not what we usually call content management, even though Application Center handles content. Content management is covered in another Chapter 5 of the book, but briefly this is more about the administration of the content on the Web pages in an application. Content management applications often help in managing who has access to update a specific Web page and what guidelines exist for the page. Microsoft has a tool called Microsoft Content Management Server to help do this, but other tools like EPiServer might be a better solution in many cases. By setting user rights and client rights, and creating Web page templates with the content management tool, you can control the look of the Web site and make sure design rules are followed by the people allowed to update the pages. You can also restrict who gets to see which page and what parts of a page they are allowed to see. This process is known as personalization of a Web page and is often managed with the help of a content management tool.
So as you can see, there is a difference between the content management provided by Application Center and the content management provided by other tools. But the two techniques are often used in conjunction with each other to make life even easier for administrators.
To maintain a high availability of your cluster, you need to know certain things. You need to have a thorough understanding of not only when your clusters are running smoothly, but also when they are having a bad day and performance is compromised. To be able to understand this, you must be able to comprehend events and performance metrics. When some events occur, it might be a clue to a pending failure of the cluster, and if you do not see the signs, you cannot prevent it from happening. If you do not know that a constantly high CPU load means it might be time to add more power to the cluster by perhaps adding one or more servers, you are in big trouble. And, of course, if you are a system administrator and let your clusters fail, and thereby let company applications fail, your employer will not be happy.
To prevent this from happening, Application Center provides a rich set of features that helps you detect, analyze, and fix performance and availability problems.
Application Center continuously records and displays different aspects of the health and functionality of your cluster (see Figure 3-15). These aspects are
Events
Performance counters
Server health
Member status
Events and performance metrics are stored on each member. You can use performance metrics to view these in real time or aggregated over a longer period. This makes it possible for you to spot immediate problems or discover long-running trends. Since Application Center is a single point of monitor, you can also use it to collect events from many member servers in a single view and thereby expedite the filtering of events and processing of the same for an administrator.
You can also set numerous thresholds for specific events and information and get notified when a threshold is reached. You can set thresholds on event logs, Windows service failures, HTTP calls, WMI events, and more. This functionality is provided by Microsoft Health Monitor 2.1, which is distributed with Application Center. You can set up possible actions when these thresholds are reached. We have mentioned notification already, but predefined scripts can also be run if necessary.
So who or what generates this monitoring data anyway? Well, several actors are involved in this process. Different applications, Windows services, and other objects are responsible. Here are a few:
Application Center itself: Of course, most events are generated by Application Center, since it is one of the main actors involved. If it did not keep an eye on itself, it really would not be of that much use to you.
The operating system: For example, Windows 2000 Server or any other OS in the Windows family produces many events that lets you know the status of the OS and Application Center.
Health Monitor: If you want to be able to set thresholds for events and respond to them with various actions, Health Monitor must be able to notify you, run scripts, or send other events when thresholds are met. Application Center collects a large amount of data from Health Monitor by default. There are also ways to expand these collectors by creating new ones, or installing Health Monitor sample data collectors. This is useful if you do not find the ones supplied adequate for your situation.
Windows Management Instrumentation (WMI): This is a management infrastructure that provides standardized methods for accessing events and other monitoring and management information across an enterprise environment.
So let us look in more detail at how the process of Application Center monitoring is carried out. There are four steps in this process:
Data generation
Data logging
Data summarization
Data use
Figure 3-16 shows an overview of how Application Center, Health Monitor, and the operating system generate events and performance counters. It also shows how this data is provided to WMI.
Application Center subscribes to some of these WMI events and logs them for later use in the user interface. Microsoft Application Center is also smart enough to provide its own events with extended and troubleshooting information, a feature called event details.
During Application Center setup, if you choose to install Application Center Event and Performance Logging (see Figure 3-17), a SQL Server 2000 database is also installed. This is, as we are sure you have already guessed, where Application Center stores the logged data.
Because the infrastructure of this database is exactly like an ordinary SQL Server and also provides the same functionality, you can use the same ways of accessing this database as you would if you were to access a SQL Server. This means you can use SQL queries and stored procedures to access data. Other data accessing methods, like ADO.NET, are also possible to use, giving you the flexibility to choose for yourself the way you want to retrieve data. If you do not want to go through the trouble of making these queries, you can use the Application Center user interface to display the information you are looking for. The important thing to remember here is that these other accessing methods are available so that, when the user interface does not show you what you want, you can find the information yourself.
One benefit of storing the monitoring data in a database is that you can display information more flexibly. You can also let other applications and services access the data.
In the Application Center Event View, you can choose to view the data points for different time frames (see Figure 3-18). Application Center scans logs for 1-minute, 15-minute, and 2-hour time frames. The older the information is, the less detail it provides. This happens because as data is summarized over a longer period of time, say one day, there is no way of keeping the same level of detail as you can for the 1-minute interval. These logs are cleared by default after a specified number of days. A property called "Keep logged events for (days)" is available in the Event Properties dialog box.
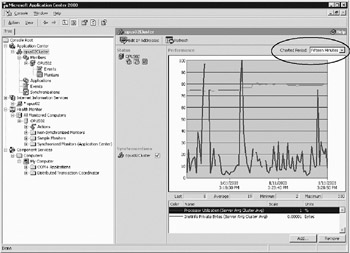
As you have seen, Application Center collects a large amount of data in a detailed format about the cluster and its members. This data quickly grows, and lots of disk space is required to hold it. Application Center therefore summarizes this data periodically and loads it into a summarization table. Two kinds of data sets are summarized:
Event data: Data that is maintained in the log for a specified number of days as mentioned previously. The default is 15 days before any data is removed.
Performance counter data: Data that is collected every 10 seconds. This data is summarized in four intervals: 1 minute, 15 minutes, 2 hours, and daily. The whole cluster is synchronized with these time intervals.
Because the summarization changes the granularity of the data, less and less detail can be shown as the time frame grows larger. If you want to be able to see the data in greater detail later, you must collect data more often. This requires, of course, more disk space, but luckily hard drives are cheap these days. So if you decide you have enough disk space, you can archive the detailed data before it is summarized, and then you can really dive into it when you want to.
Figure 3-19 shows different ways of collecting data from Application Center logs and presenting them in a report. By using SQL queries, you can easily import the data into your favorite presentation tool and generate the reports you want to display.
But of course, you can also use Application Center Event View, Performance Chart, and Cluster Status to display information about the cluster and its members. It is also possible to customize these views.
The primary administrative user interface for Application Center is the MMC. From here you can administer local as well as remote clusters, as shown in Figure 3-20. You can also choose to connect to a specific server as well as a cluster depending on your administrative needs.
The MMC is not the only administrative tool available, however. There is also a Web-based interface, but this only has limited administrative possibilities. So if you are going to administer a remote cluster or server, you should really try to use the MMC. When you do this, you also get a secure remote connection.
If you are really into command-line commands, Application Center is equipped with a set of these, too. You can use these commands to automate administration and management of Application Center.
And, as if this were not enough, there is also a programmatic interface to Application Center that you can use to build administration of clusters in your own applications.
Let us have a look at three possible scenarios using Application Center. The point of discussing these is partly to show different ways of taking care of security in your Web applications but also to show where Application Center is useful in a solution. All clusters in these examples are run by Application Center—Web clusters as well as COM+ clusters.
The first example (Figure 3-21) shows an internal network protected by a single firewall. The Web cluster, COM+ cluster, and stager are all behind this firewall. The database is also protected only by this firewall.
In a scenario like this, both the database and the business logic in the COM+ cluster as well as the stager are potentially exposed to users from the outside. To prevent some of these security risks, it is very common to add another firewall, thereby creating a perimeter network.
Here we have added a perimeter network, as Figure 3-22 shows. This is commonly referred to as a demilitarized zone (DMZ). In this scenario, we protect the staging server and database server from being compromised by, say, a Trojan horse attack. But as you clearly see here, we have only partly solved the problem. While the database and staging server are protected behind the second firewall, we still potentially expose the business logic. The COM+ components often use role-based, or programmatic, security to keep data safe. This could be compromised if the components reside on the Web tier of our application. And we do not want to risk our business logic coming into the wrong hands, because this could jeopardize our business. We must do something about this.
In the third example, we also move the COM+ cluster behind the second firewall, as Figure 3-23 shows. Here we use CLB to even further enhance security in the Web site. An unreliable client trying to access the business logic would be prevented from doing so by the second firewall. It would instead only allow COM+ components to be created by calls from the Web tier cluster.
But we still have a few problems left in this solution. We can even further enhance security by using Web services instead of COM+. If we let COM+ calls through a firewall, it means we must open up the specific ports necessary for this traffic to be let through. We instead want to keep the firewall as closed as we can and only allow HTTP traffic through. The next example shows how this kind of solution could be designed.
Figure 3-24 shows the design of a solution where we have changed from exposing our logic as COM+ components and instead use Web services. One thing you need to understand before using this scenario yourself is that the inclusion of Web services comes with a certain penalty. Performance is negatively affected by having to use HTTP instead of COM+ calls. COM+ calls are generally faster than HTTP calls, but since in this example we are on our internal network, we have control of bandwidth usage, and we feel it is better to lose a little performance than to have too many holes in our firewall. Our own testing shows such tiny performance degradation that the move to Web services is well worth the effort just to have better security. But we strongly suggest testing such a method before deploying it.
In all of these scenarios, we could also use .NET Remoting instead of COM+ or Web services over an HTTP connection. .NET Remoting is a generic and extensible interprocess communication system. You can use it to create Web services hosted in IIS, and have the security, scalability, and state management (both session and application state) that ASP.NET and IIS offer. If you are interested in security issues over performance, you should use ASP.NET or .NET Remoting hosted in IIS. If you use any other transport protocol, you would have to handle security yourself. The same goes for using the HTTPChannel outside of IIS.
It is not possible to load balance .NET Remoting if you host it outside of IIS. This we suspect will change in the coming versions of Application Center. In the meantime, in our scenarios we must host .NET Remoting in IIS if we want to use it.
If you want to keep the IIS hosting with its security, and still get increased performance, you should definitely use the binary encoding of .NET Remoting. Our own tests as well as several others show a performance boost when using the binary formatting, even if we use the HTTPChannel.
To get absolutely maximum performance from .NET Remoting, you should use the binary formatting over a TCPChannel. But then you must be certain that you are running entirely in a secure environment, behind a firewall. So in this case, we would not recommend it, since you need to expose objects to outside your firewall. The key issue as we see it is to keep the firewalls as closed as possible. If you open up ports in them, you have a potential security risk. This is why we recommend the use of only port 80 and HTTP traffic when you need to expose objects to outside your firewalls. This limits you to the use of Web services or .NET Remoting over the HTTPChannel, of course, but you should be able to live with that.
If you need to choose between .NET Remoting using binary formatting over an HTTPChannel and traditional Web services, you should consider some issues. Both methods are scalable when hosted in IIS, but keep in mind that .NET Remoting using binary formatting over an HTTPChannel is faster than traditional Web services. .NET Remoting, however, demands that the client have access to the .NET Framework to give full access to all its features, and if you need interoperability with other platforms, this is not always possible. However, you could use a J2EE implementation called JNBridge that connects .NET with Java, but we have not tried this ourselves. You could think of .NET Remoting as a substitute for DCOM, where you make many calls to a component during the session and need more extensible features than you can get from Web services. Especially when you have communication between .NET applications that do not have to cross a firewall, .NET Remoting is very useful, and you can be certain both ends support the .NET Framework in that case.
If you want a client not using .NET Remoting plumbing to access your Web services created from .NET Remoting objects, you need to think about some things first. If you carefully pare down your endpoints to bare-bones data types and semantics, you could use them. If you do not restrict parameters to built-in simple types and your own data types, you cannot interoperate your .NET Remoting Web services with other Web services implementations. You also need to avoid client-activated objects and events in that case. What have you really got left then? Not much more than a traditional Web service could offer. So if you want to support a wide range of clients, you should use traditional Web services.
A good suggestion is choosing Web services by default, even in a homogeneous environment, between internal systems and subsystems. Use .NET Remoting only in those special cases where you really need it. This would be when you know that the client supports the full .NET Framework, and you need the extensible features of the full Framework. This could also be when performance is an issue, since .NET Remoting generally is faster than Web services.
Our recommendation for using .NET Remoting with some transport protocol other than HTTP is to make sure the client is placed behind the same firewall as the Remoting object. If it is not, you need to open up the firewalls, which gives you a potential security hole. You would also need to implement security yourself in code, since you cannot use the built-in features of IIS in this case.
Now you have come a few steps down the road of security. But there is a lot more you can do, as this book will show. One way to enhance security more would require you to dive into the world of Windows and network security, which is beyond the scope of this book. Application Center is based on the services provided by Windows and Internet Information Services. In Application Center, you find very few user-configurable security settings. You must therefore learn and understand Windows security to fully secure your network. It is also essential that you keep in close cooperation with the people who understand these things the best: the system architects and the administrators. But let us not forget the software developers. A lot also can be done to enhance security in the code.
These are a few different scenarios using Application Center. If we personally wanted to choose a solution for our own network, we would definitely choose Example 4, since the benefits are great with this setup. But in the end, it is up to each company and each Web site to set its own standards.
Imagine you are handling a large Web cluster using Network Load Balancing and Application Center. On this cluster, you run an online store selling books. Customers can browse the products and add interesting items to their shopping cart. Since you are using Network Load Balancing, all client requests are subject to load balancing. When the customer first establishes a session on the Web site, he or she is directed to a specific server. It is Network Load Balancing that forwards the request to this server. To maintain session state, all coming requests from this customer must be redirected to the server where the session was established. But since Network Load Balancing redirects client requests to different servers, the customer is not guaranteed to end up at the server where the session was started. This means that the items in the shopping cart might disappear suddenly, since the new server taking care of the request has no idea of who the customer is and that he or she has added items to the cart. If this happens, the customer is likely to take his or her business elsewhere, and you lose the sales.
So how can you solve this problem? Well, there are several ways to do this. The Application Center solution is to provide a request forwarder. The request forwarder makes sure all HTTP requests are forwarded to a particular server so that session state is maintained. It also makes sure the following requests are forwarded to the cluster controller (because if they were not, synchronization of the cluster would overwrite updates):
Internet Information Services (IIS) administration requests
Microsoft FrontPage publishing
Web Distributed Authoring and Versioning (WebDAV) publishing
Web-based administration requests
Let us concentrate on HTTP requests. How does the request forwarder work? The forwarder is an ISAPI filter and extension. This means it positions itself in front of the IIS and checks incoming requests before they are handled by the Web server, but after they have been load balanced by Network Load Balancing. Based on the information in the request, the request forwarder sends it to the correct cluster member. For this to work, you need to have set up a few things. First of all, you need to understand request forwarding only applies to sites that use Active Server Pages (ASP) session state. This is set up in IIS by enabling session state in the application configuration for the site. To save you time, this is done by default. After that, you need to make sure the clients accept cookies, since the request forwarder uses these to maintain session state by associating clients with a specific cluster member and writing the information to the cookie. Following requests from a client will be forwarded to a particular cluster member based on the information in the cookie.
This scenario presents some problems. What if the client rejects all cookies? It would be hard to use this solution if that were the case.
Performance is also slightly impacted by the request forwarder, since requests are processed after they have been load balanced.
If you want a scalable solution with good performance, our advice is to avoid use of session state with load balancing. Solve the problem some other way.
One other solution might be to keep session information in a SQL Server database. If you choose to do this, you must keep state information in a cookie or in the URL header. This way it does not matter which cluster member a client request is redirected to. You can always find session information based on the state information. You should also build a check in your Web pages that investigates whether the client accepts cookies; if not, keep state in the URL header instead. This solution is excellent when you need a reliable solution, since you can cluster the SQL Server to handle failure scenarios.
To even further enhance performance, you should disable or even uninstall the request forwarder completely. This way you get rid of the overhead caused by it.
When you use ASP.NET, you can take advantage of the built-in features for session state handling. In ASP.NET, session state is independent from the ASP.NET host process. This means ASP.NET session state is run in a separate process, and ASP.NET can come and go as it likes, while session state remains.
ASP.NET also has better support for handling your Web server farms. The new out-of-process session state allows for all servers in a farm to share a session state process, which is what you want when you cannot guarantee that a client is redirected to the same server for its entire session. To achieve this, you change the ASP.NET configuration to point to a common server. There are two options for configuring the out-of-process session state: memory based (using a state server) and SQL Server based. Cookie handling has also been simplified in ASP.NET. Now you only change a configuration setting to apply cookieless sessions. This could be complex to achieve in legacy ASP.
Application Center is great for handling large clusters. It enhances manageability and presents Component Load Balancing that helps you scale not only the Web server, but also business logic. One of its drawbacks is that it might not be the perfect tool if you choose third-party load balancers since the integration with these devices is not that great yet.
You have also seen that Application Center provides the request forwarder to help you maintain state in a load-balanced solution. But a good rule is this: For better performance and scalability, do not use state in such a solution. For smaller sites, it might be a good way to solve session state, but in a large cluster with heavy traffic, you are better off without it.
Up until Release Candidate 2 of Windows Server 2003, we have not been able to install Application Center on this platform. We suspect that a service pack or new version of Application Center will correct this.